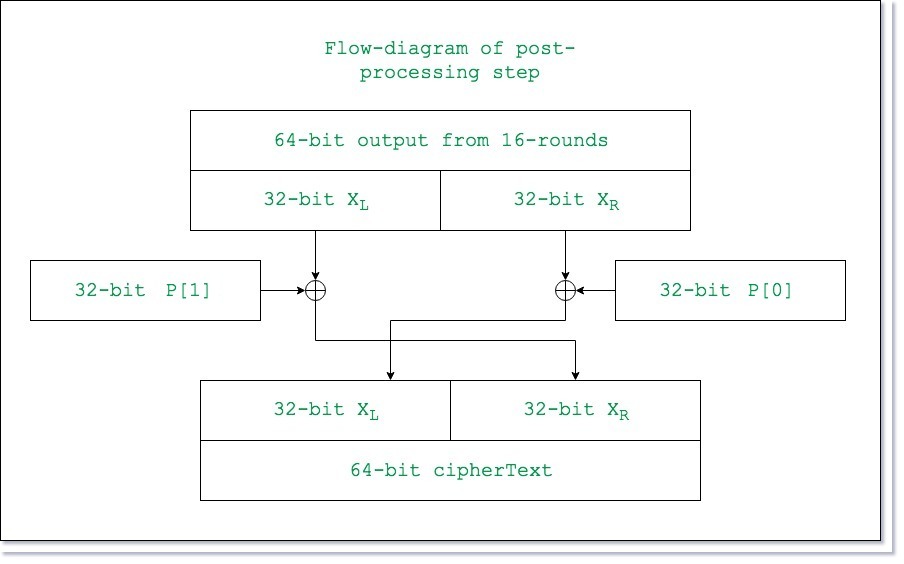
Key Algorithm Among Us, Pgp Keys Software Security And Much More Threatened By New Sha1 Exploit Ars Technica
Key algorithm among us. Among Us lately has been a very by famous games, perhaps it is because its extremely funfull game to play. Becoming an impostor is the dream by player in Key algorithm among us game. Because you can kill another crewmate and It is funny to see friends fighting among others to vote for the impostor, and sometimes they start of to argue who is Is the true Impostor Key Algorithm Among Us.
More From Key Algorithm Among Us
- Impostor Among Us Jugar
- Among Us Names To Use
- Teal Among Us
- Neon Red Amoung Us Logo
- Imposter Knife Among Us
If you are searching for download Imposter Knife Among Us you've reached the perfect place. We ve got 104 download links about imposter knife among us including apk, cheat, cheat apk, wallpapers, and more. In such page, we additionally provide number of mp3 out there. Such as png, jpg, animated gifs, pic art, symbol, blackandwhite, transparent, etc.
Incoming Search Terms:
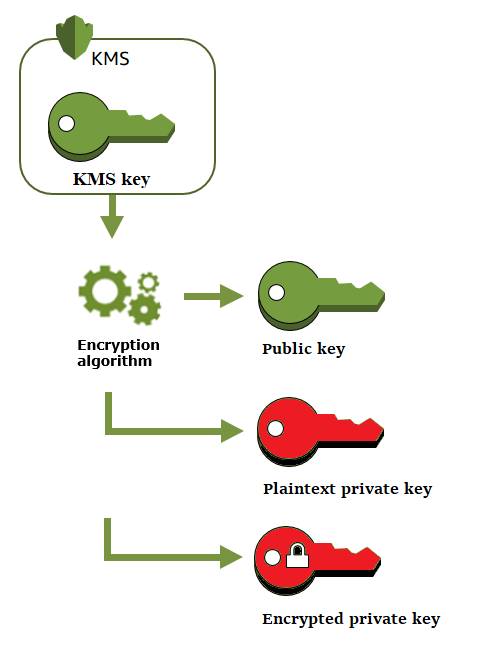
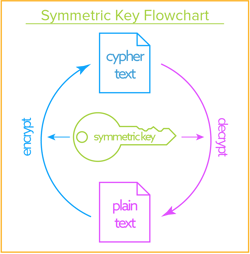
- Key Cryptography An Overview Sciencedirect Topics Imposter Knife Among Us,
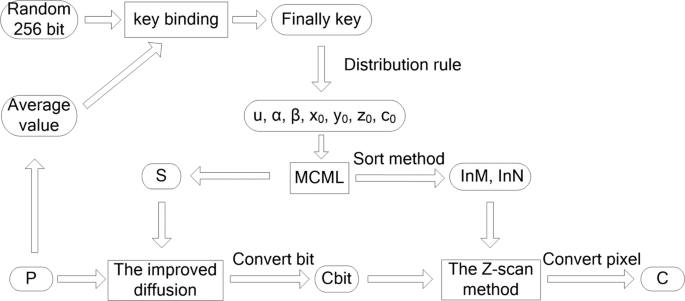
- A New Image Encryption Scheme Based On Coupling Map Lattices With Mixed Multi Chaos Scientific Reports Imposter Knife Among Us,
- International Data Encryption Algorithm Wikipedia Imposter Knife Among Us,
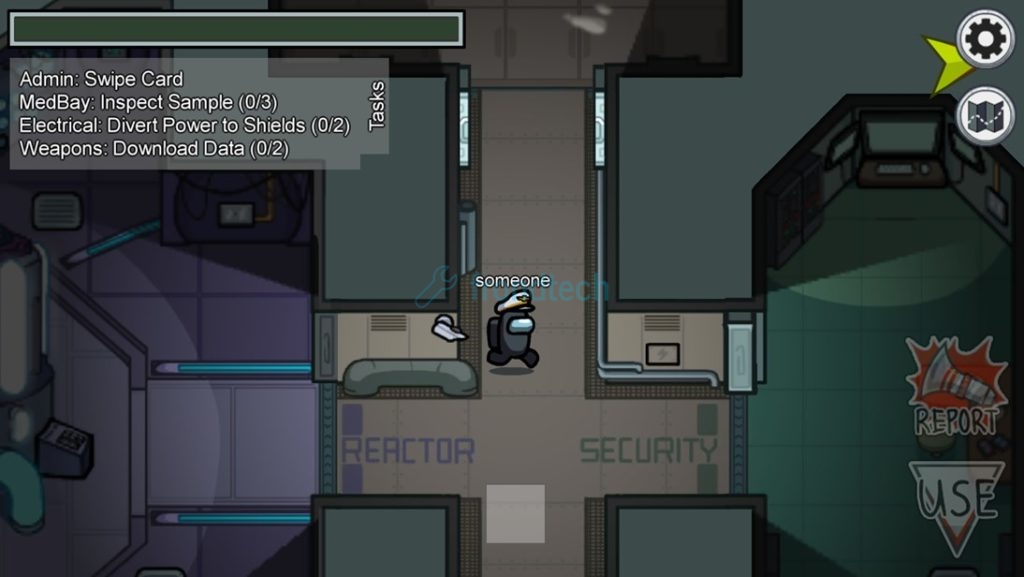
- The Skeld Tasks Guide Among Us Wiki Guide Ign Imposter Knife Among Us,
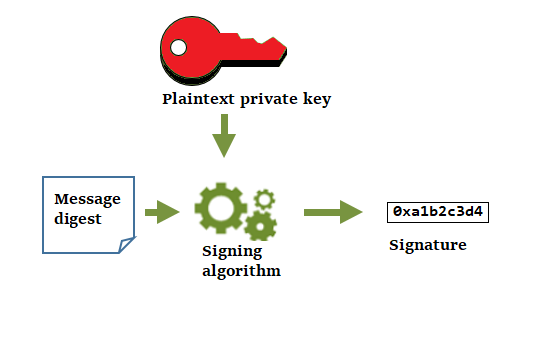
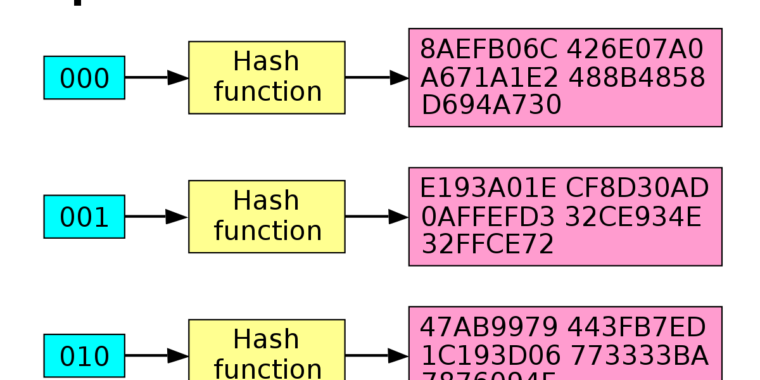
- Cryptography Encryption Hash Functions And Digital Signature By Eray Altili Medium Imposter Knife Among Us,
- Among Us Polus Tasks Guide Android Central Imposter Knife Among Us,